The Windows Registry (system registry) is a hierarchical (tree) database containing records that define the settings and customizations of Microsoft Windows operating systems.
The registry as it appears when viewed by the registry editor is formed from data whose sources are registry files and hardware information collected during the boot process. The term Hive is used to describe registry files in English. Microsoft documentation translates this term as Shrub.
Main files responsible for the formation of the registry
Registry files are created during the operating system installation process and are stored in a folder:
%SystemRoot%\system32\config (usually C:\windows\system32\config).
For Windows operating systems, these are files named:
- system
- software
- sam
- security
- default
- components
- bcd-template
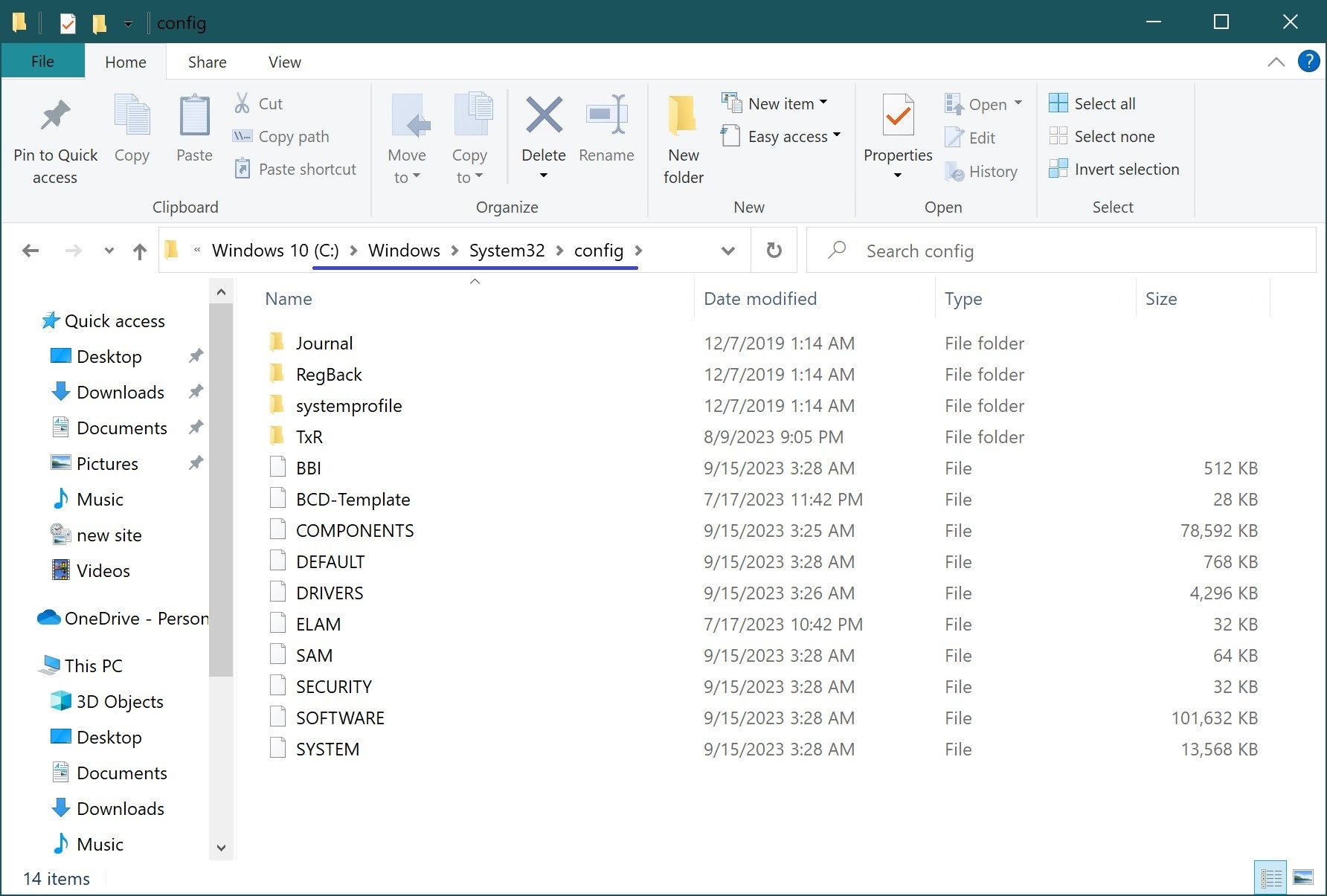
In Windows Vista, Windows 7, Windows 8, Windows 8.1, Windows 10, the registry files are located in the \Windows\system32\config directory and have the same names, but these operating systems have added a new registry section for storing Boot Configuration Data with the name BCD00000000.
The data file for this partition is named bcd and is located in the hidden Boot folder of the active partition (the partition from which the system is booted).
Usually, during a standard Windows installation, an active partition of small size (from 100 to 500 megabytes depending on the operating system) is created, which is hidden from the user and contains only service data for booting the system – boot records, boot manager bootmgr, boot configuration store BCD, localization files and memory test programs
The location of the bcd heap depends on how the system boot loader is configured when the system is installed, and may be on the same partition as the Windows directory.
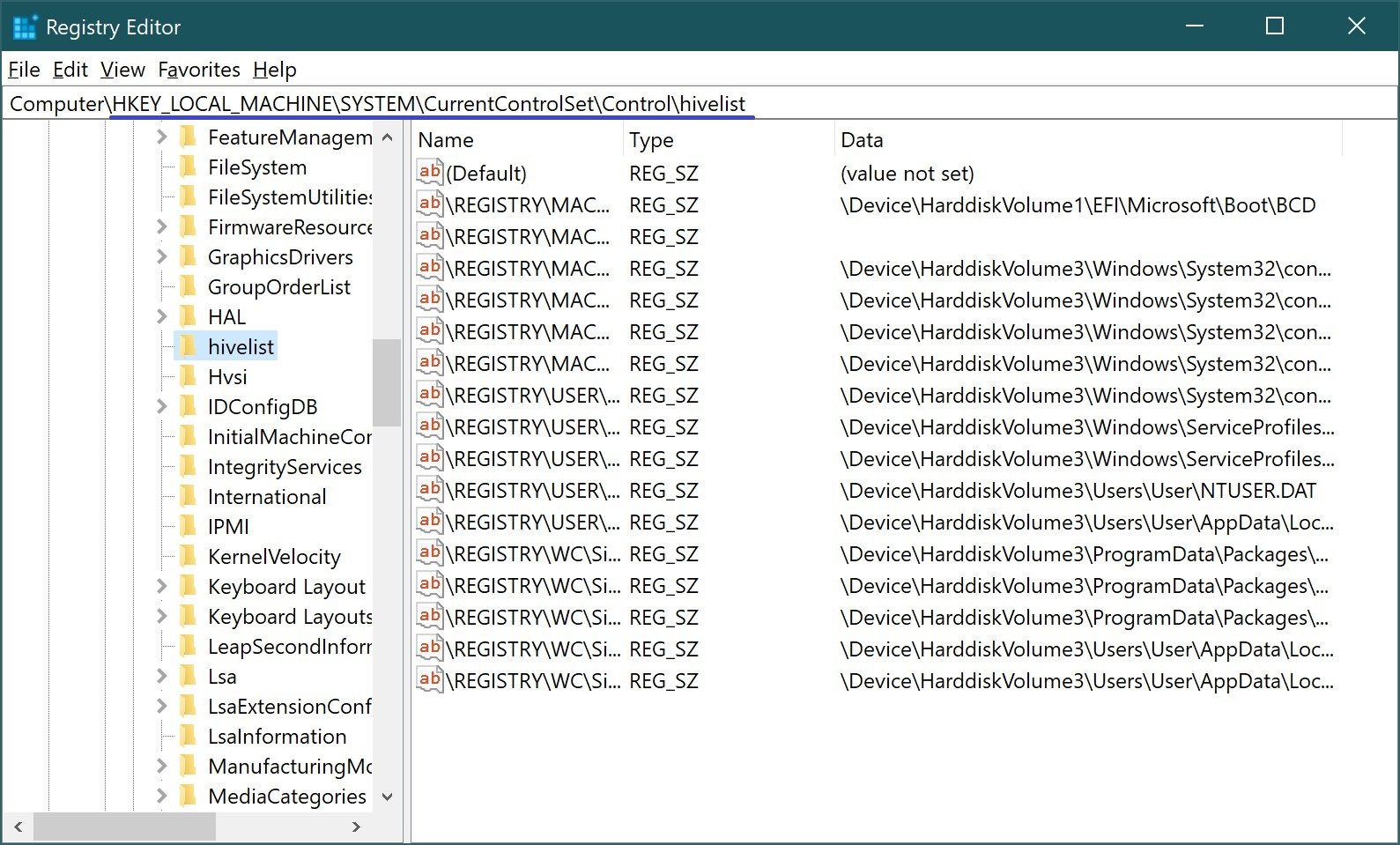
The location of the registry files in any version of Windows can be viewed using the Registry Editor, under:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\hivelist
This section stores information about all clusters, including user profiles, with links to their location in the Windows file system.
Registry structure
The Windows Registry has a tree structure and consists of 5 main registry sections:
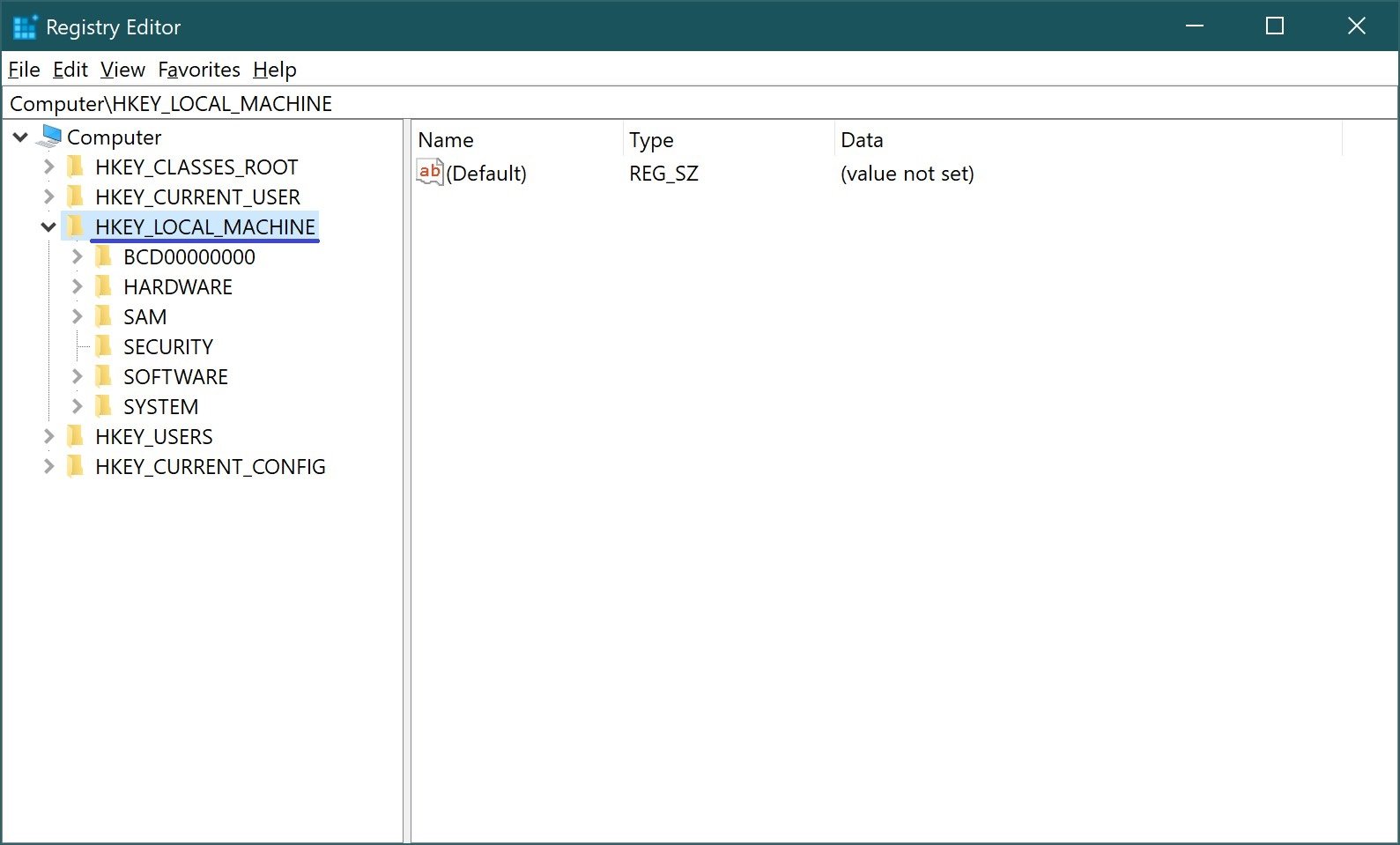
HKEY_LOCAL_MACHINE (HKLM) is the largest section of the registry. It contains all the basic settings for the operating system and the computer hardware and software. The information contained in this section applies to all users who log on to the system.
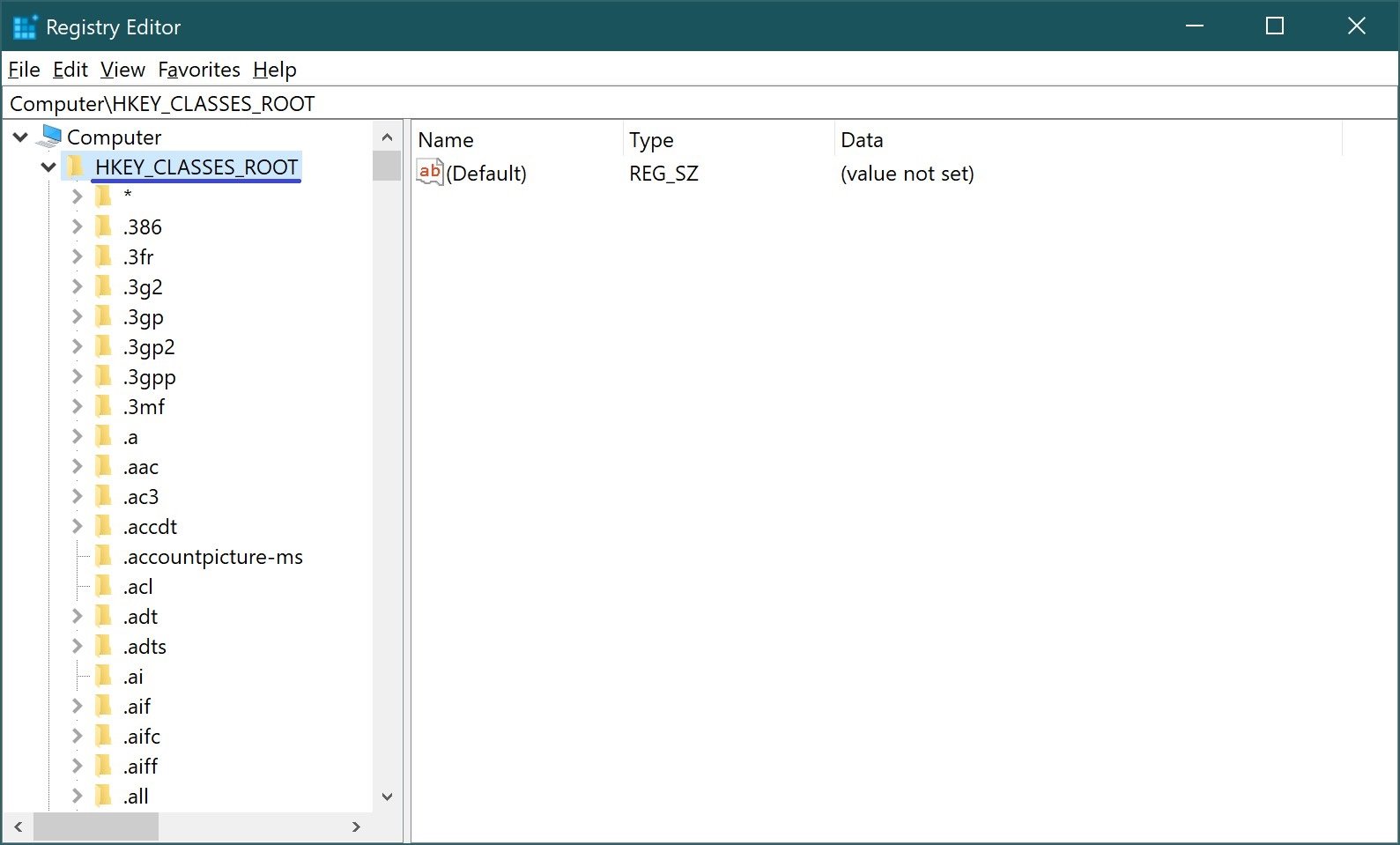
HKEY_ CLASSES_ ROOT (HKCR) – contains associations between applications and file types (by file extension). In addition, this section contains information about registered file types and COM and ActiveX objects. In addition to HKEY_ CLASSES_ ROOT, this information is also stored in HKEY_LOCAL_MACHINE and HKEY_CURRENT_USER.
The HKEY_LOCAL_MACHINE\Software\Classes section contains default settings that apply to all users on the local computer. The settings contained in HKEY_CURRENT_USER\Software\Classes override the default settings and apply only to the current user. The HKEY_CLASSES_ROOT section includes data from both sources.
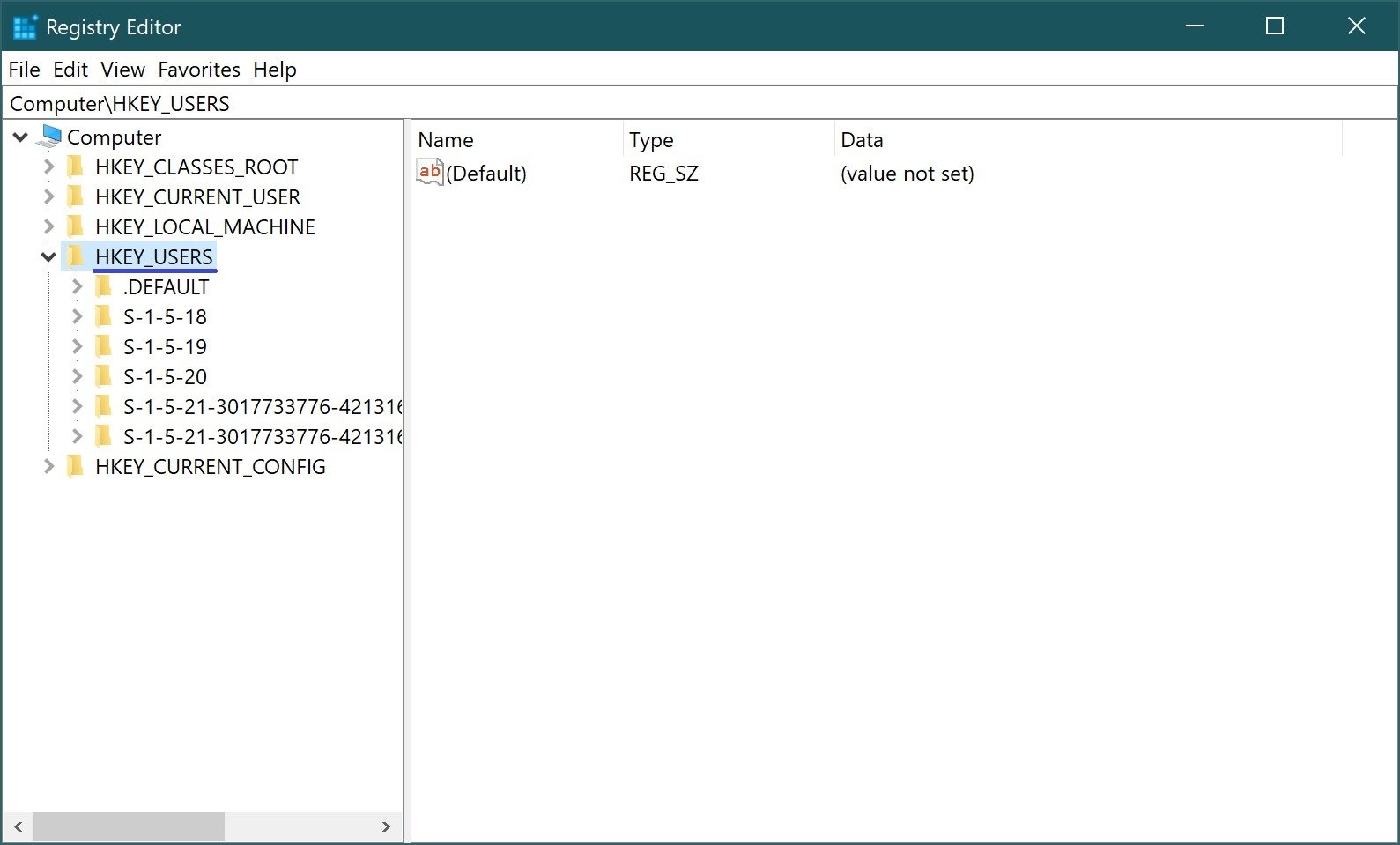
HKEY_USERS (HKU) – contains environment settings for each of the loaded user profiles, as well as for the default profile. HKEY_USERS contains a sub-section \Default, as well as other sub-sections defined by the Security ID (Security ID, SID) of each user.
HKEY_CURRENT USER (HKCU) – contains environment settings for the currently logged in user (environment variables, desktop settings, network settings, applications and connected devices).
This section duplicates the information in HKEY_USERS\user SID, where user SID is the security identifier of the user currently registered in the system (you can find out the SID of the current user by typing whoami /user in the command line).
HKEY_CURRENT_ CONFIG (HKCC) – contains settings for the current hardware profile. The current hardware profile includes sets of changes made to the standard device configuration specified in the Software and System subsections of the root HKEY LOCAL_MACHINE section.
Only changes are reflected in HKEY_CURRENT_CONFIG. In addition, information in this section can be found in HKEY_LOCAL_MACHINE\System\CurrentControlSet\ HardwareProfiles\Current.
Data in the registry is stored in the form of parameters located in registry keys. Each parameter is characterized by name, data type and value.
Main data types used in the registry
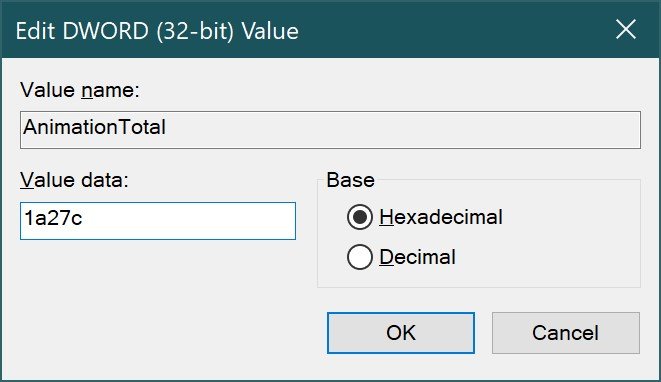
REG_DWORD is a 32-bit number. This data type is used by many device driver and service parameters. Registry editors can display this data in binary, hexadecimal, and decimal formats.
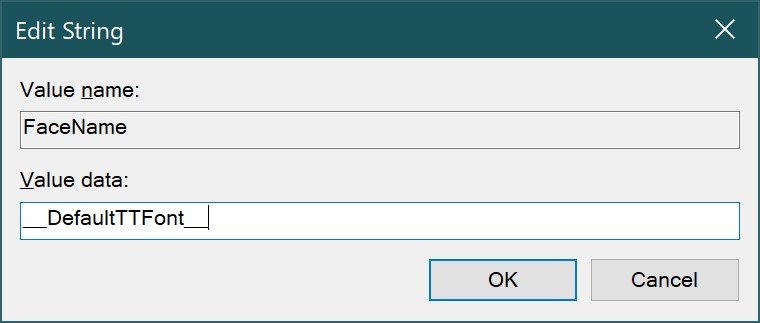
REG_SZ – A text string in a human-readable format. Values representing component descriptions are usually assigned to this data type.
REG_EXPAND_SZ – Extensible data string. This string is a text containing a variable that can be replaced when called from the application side, e.g. used to record environment variables.
REG_MULTI_SZ – Multiline field. Values that are actually lists of text strings in a human-readable format usually have this data type. The strings are separated by the NULL character.
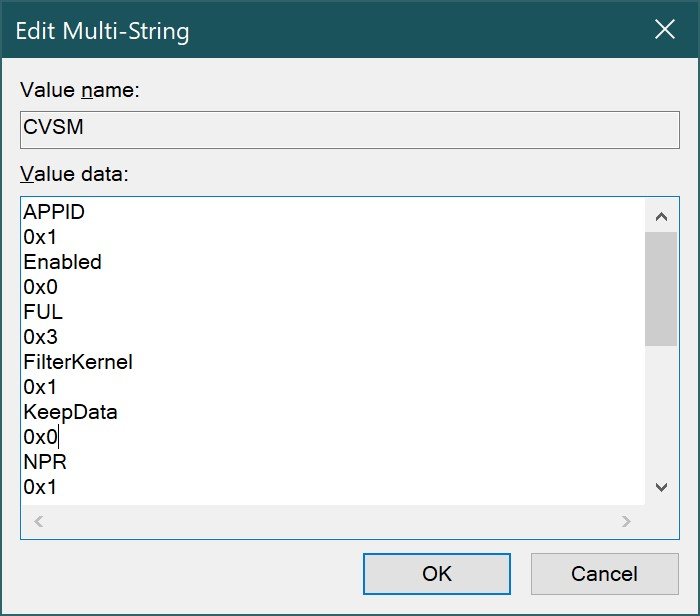
REG_BINARY – Binary data. Most hardware components use information that is stored as binary data. Registry editors display this information in hexadecimal format.
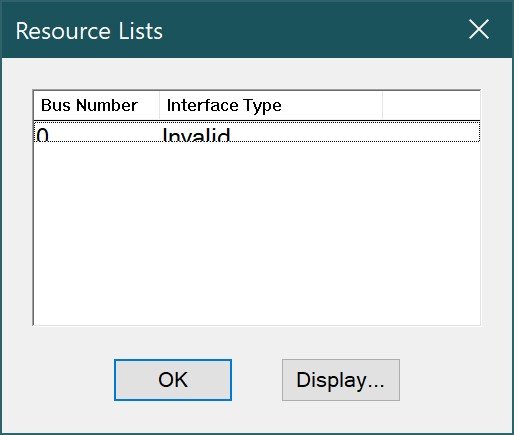
REG_RESOURCE_LIST – List of hardware resources. Applies only in the HKEY_LOCAL_MACHINE\HARDWARE branch.
You may also sometimes see these types of registry data:
- REG_RESOURCE_ REQUIREMENTS_LIST – List of required hardware resources. Applies only in the HKEY_LOCAL_MACHINE\HARDWARE branch.
- REG_FULL_RESOURCE_ DESCRIPTOR – Hardware resource descriptor. Applies only in the HKEY_LOCAL_MACHINE\HARDWARE branch.
- REG_LINK – Unicode symbolic link. This data type is interesting because it allows one registry item to refer to another key or parameter.
- REG_QWORD – 64-bit number.
- REG_DWORD_ LITTLE_ENDIAN is a 32-bit number in “little-endian” format, equivalent to REG_DWORD.
- REG_DWORD_BIG_ ENDIAN – 32-bit number in big-endian format.
- REG_QWORD_LITTLE_ ENDIAN – 64-bit number in “sharp-endian” format. Equivalent to REG_QWORD.
- REG_NONE – Parameter has no defined data type.
Registry interaction with the operating system
When you start your computer, the hardware recognizer puts a list of the devices it detects into the registry. Typically, hardware recognition is performed by the Ntdetect.com program and the operating system kernel Ntoskrnl.exe.
At system startup, the system kernel retrieves information from the registry about the device drivers to be loaded and the order in which they are loaded. In addition, the Ntoskrnl.exe program sends information about itself (e.g. version number) to the registry.
During the system boot process, device drivers communicate boot parameters and configuration data with the registry. The device driver reports the system resources it uses, including hardware interrupts (IRQ) and memory access (DMA) channels, so that the system can include this data in the registry.
By the way, the registry allows you to create several hardware profiles. A hardware profile is a set of instructions that can be used to tell the operating system which device drivers should be loaded when the computer starts up. By default, the system creates a standard hardware profile that contains information about all hardware detected on the computer.
When a user logs in, user profiles are loaded. All information related to a specific user name and associated permissions is stored in the registry. A user profile defines individual system settings (display resolution, network connection settings, connected devices, and more). Information about user profiles is also stored in the registry.
When installing applications. Each time an installer runs, new configuration data is added to the registry. All installers must start their work by reading information from the registry to determine if the components they need are present on the system. In addition, the system registry allows applications to share configuration information, which gives them more opportunities to interact. An application must actively and correctly use the registry and be able to correctly remove it without affecting components that may be used by other programs (libraries, program modules, and so on). This information is also stored in the registry.
When administering the system. When a user makes changes to the system configuration using system administration tools (such as the Control Panel or MMC snap-in), all changes are immediately reflected in the system registry. In fact, administrative tools are the most convenient and safe means of modifying the registry. By the way, the registry editor (regedit.exe) can also be considered as an administrative tool, because all changes to the system can be made directly by editing the registry.
During the booting and operation of the operating system, registry data is constantly accessed, both read and written. Registry files are constantly changing because not only the system, but also individual applications can use the registry to store their own data, settings, and preferences. In other words, accessing the registry is one of the most common operations. Even if the user is not working on the computer, registry accesses are still performed by system services, drivers, and applications.
Violation of the integrity of registry files (data structure violation) or incorrect values of some critical parameters can lead to system crash. Therefore, before experimenting with the registry, make sure that it can be saved and restored.